 With the approach of the transition of the Ethereum cryptocurrency to POS consensus instead of POW mining, the issue of the stable operation of the future Beacon Chain POS network is becoming more and more acute. The main protection mechanisms are fines for an idle node, Slashing - exclusion from the network of the validator for violating the rules of operation and leakage of inactivity. If most of the network participants are familiar with the first two punishments for validators, then not many crypto enthusiasts have heard about the punishment called inactivity leak.
With the approach of the transition of the Ethereum cryptocurrency to POS consensus instead of POW mining, the issue of the stable operation of the future Beacon Chain POS network is becoming more and more acute. The main protection mechanisms are fines for an idle node, Slashing - exclusion from the network of the validator for violating the rules of operation and leakage of inactivity. If most of the network participants are familiar with the first two punishments for validators, then not many crypto enthusiasts have heard about the punishment called inactivity leak.
Penalties and slashing in the Beacon Chain help to deal with isolated cases in the incorrect operation of one or another validator, reducing the balance of the validator or completely excluding it from the network with the imposition of a large fine. These two methods are very effective against isolated cases, but will not be able to withstand a massive attack with many validators when there are more than 30% of invalid validators in the network. By itself, such a massive attack on the Beacon Chain network can occur intentionally, which can be very expensive and often impractical. But it is also possible that there is an error in the code of the validator (client) program, which is activated independently when certain events occur or is called specifically for hacking.
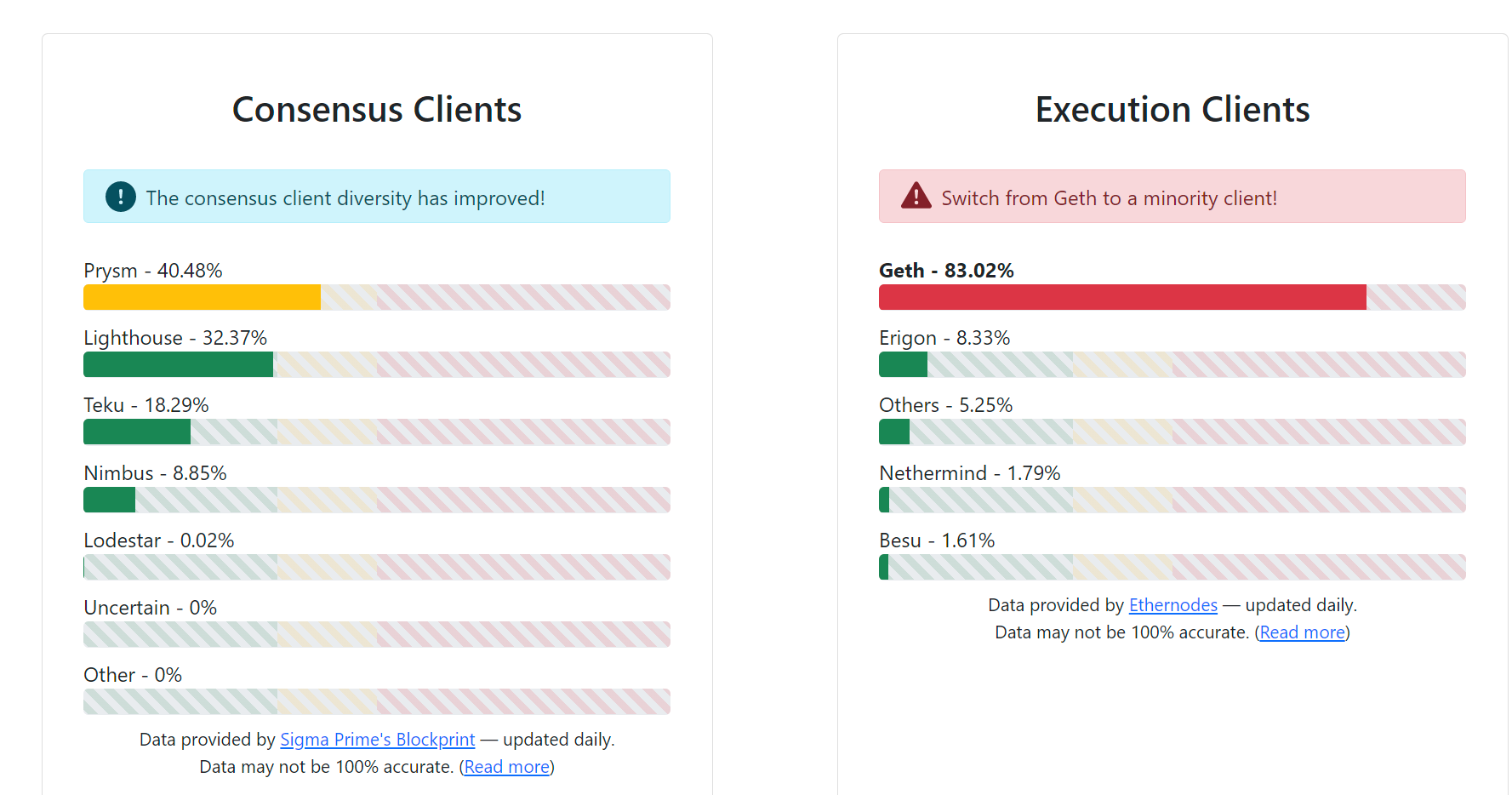
It is worth noting that at the moment there are already 6 different clients for running the server with the Ethereum 2.0 validator: Prysm, Teku, Nimbus, Lodestar, LightHouse and Grandine. Such a variety of clients for ETH2 is not accidental, because. there will be less chance of finding the same error in the code of different clients, written in different languages and by different people.
However, the presence of different clients does not guarantee that in reality all clients will be used evenly, which actually happened in 2021 when one Pryzm client was used by more than 60% of all validators. What practically put an end to the security of the entire Ethereum 2.0 network if the developers of this software made a mistake in the program code. In this case, it will no longer matter if this mistake was made intentionally or not, because. a critical failure will be reached due to which the credibility of the Ethereum cryptocurrency will be undermined, which must be avoided at all costs.
Actually, for this, they introduced such a protection mechanism as inactivity leak. This protection lies in the fact that not single validators are disconnected from the network, but all validators that have a client installed with an error in the program code. This mechanism is activated if this client in the total mass has a share of more than 1/3 of all clients in the Beacon Chain network. When disabled, the validator will receive a penalty until it upgrades its client version or switches to another client. Moreover, the longer the validator works with an error, the greater the penalty. For example, the Pryzm client now has a share of 40% of all clients in the ETH2 network, and LightHouse - 32%, which is already critically high and can lead to a serious failure when errors are detected in the work on these clients.
Ideally, there should be at least 5 different clients with equal shares in the working Beacon Chain.
You can read more about the inactivity leak in the Beacon Chain network at this link.
When choosing a client for your validator, first of all pay attention to this parameter and choose a client that has less than 30% of the network. Thus, you will contribute to the overall stability of the entire Ethereum 2 network.
You can also change the software from Pryzm to the less popular Nimbus for an already working validator using instructions for any transfer option on the ClientDiversity.org website
For the ETH1 network, the GETH client has 83%, which does not prevent the current network from working, because. security is determined to a greater extent by the mining of the Ethereum cryptocurrency on video cards and ASICs.
You can create your own validator only with 32ETH, which is quite expensive, so ETH2 staking services are now popular. With the help of which you can participate in POS ETH2 with almost any amount. To give an analogy, staking services are pools in the world of POW mining that combine many small miners into one large one.
The well-known Binance exchange has its own Ethereum 2 staking service (0% commission), which you can use if you are interested in ETH POS mining. Binance has currently launched about 10% of all validators, which is about 40,000 validators at 32ETH each.









